An Active Ids System Often Performs Which Of The Following Actions
An active ids system often performs which of the following actions. Which HIDS component is responsible for monitoring the activities on a system. What does an IDS that uses signature recognition use for identifying attacks. IDS sensor response actions are less helpful in stopping email viruses and automated attackers such as.
Update filters to block suspect traffic 10GBaseLW. Actions to be taken to reestablish normal operations. Rack mounted server D.
2-Update filters to block suspect traffic-Request a second logon test for users performing abnormal activities-Performance reverse lookups to identify an intruder-Trap and delay the intruder until the authorities arrive. Allow UDP port 22 outbound C. The MAIN difference between an IDS and an IPS is the.
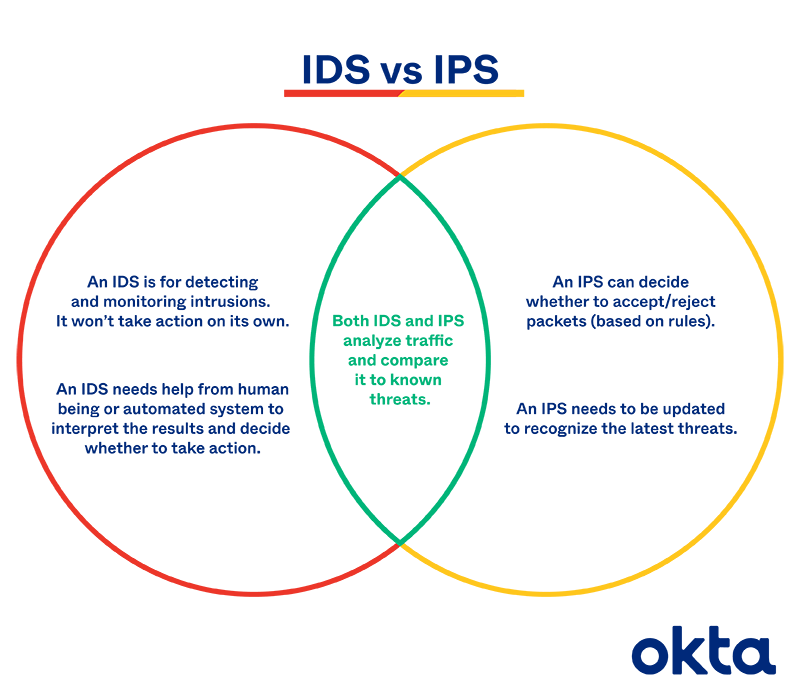
Scope definition phase 53 Which of the following analysis techniques derive system models from existing system or discovery prototypes. IDS blocks malicious activity while the IPS only alerts about malicious activity. ISSC362 Week 8 Quiz Question 1 of 15 Which of the following properly describes an IDS system.
Which of the following operations is not supported by Active Directory. 52 All of the following are phases of systems analysis except 1. Which of the following actions should be taken on the new firewall.
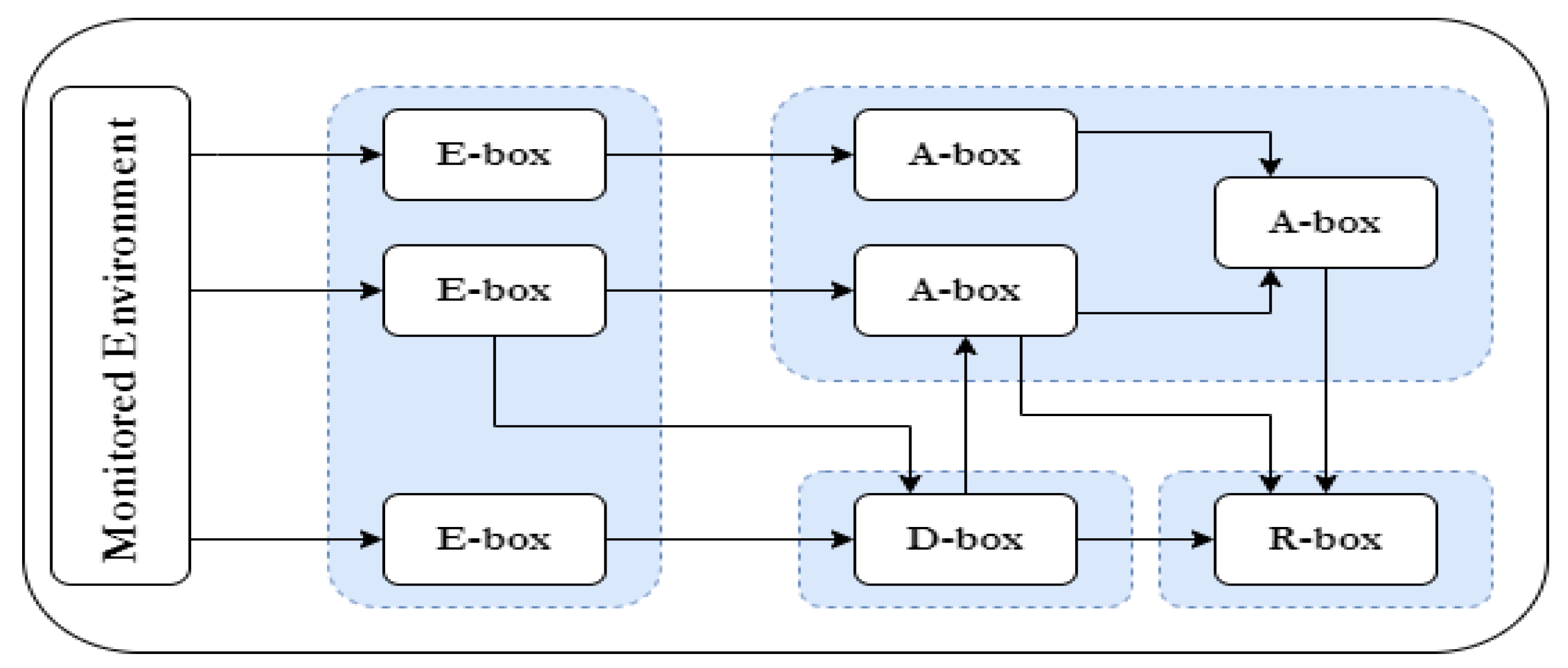
Actions to be taken in advance of an occurrence or undesirable event Actions to be taken at the onset of an undesirable event to limit damage loss and compromise Actions to be taken to restore critical functions. Problem analysis phase 5. Another kind of system is the Intrusion Prevention System or IPS.
IPS blocks malicious activity while the IDS only alerts about malicious activity. Rapid architected analysis 2.
Terminate the TCP session that has been exploited.
52 All of the following are phases of systems analysis except 1. Service level agreement Static 1. Actions to be taken in advance of an occurrence or undesirable event Actions to be taken at the onset of an undesirable event to limit damage loss and compromise Actions to be taken to restore critical functions. Design analysis phase 4. Based upon these alerts a security operations center SOC analyst or incident responder can investigate the issue and. An organization has installed a new firewall. Update filters to block suspect traffic 10GBaseLW. Host-based intrusion detection system HIDS analyzes system state system calls file-system modifications application logs and other system activity. Requirements analysis phase 3.
You want the system to take immediate action to stop or prevent the attack if possible. Which of the following systems is able to respond to low-level security events without human assistance. An active IDS system often performs which of the following actions. Which of the following operations is not supported by Active Directory. What does an IDS that uses signature recognition use for identifying attacks. An IDS can be part of a larger security tool with responses and remedies but the IDS itself is simply a monitoring system. Rapid architected analysis 2.
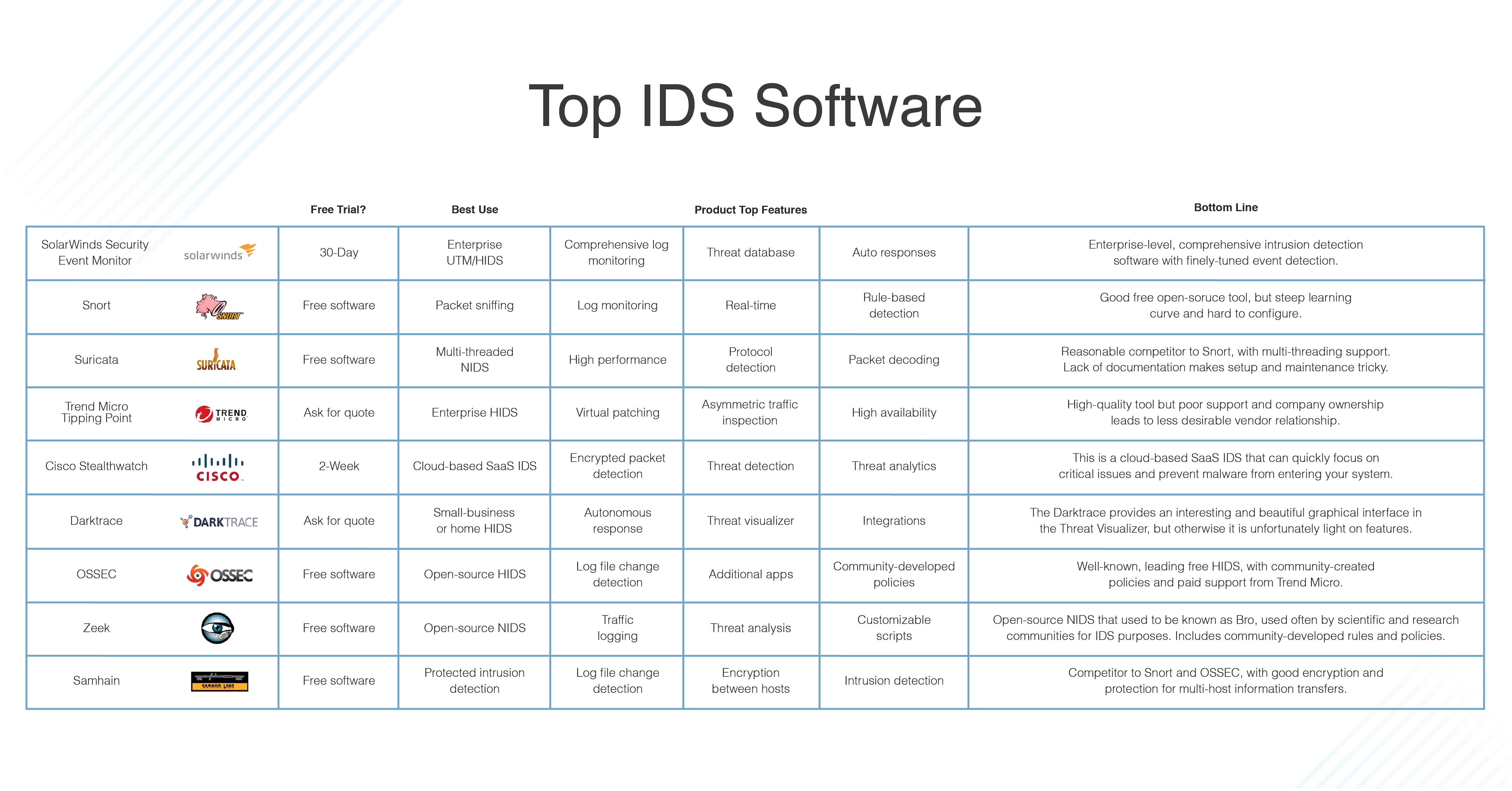
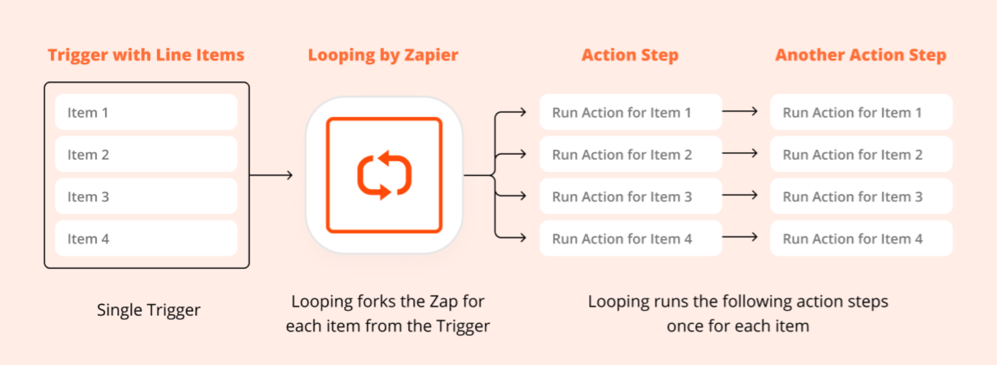
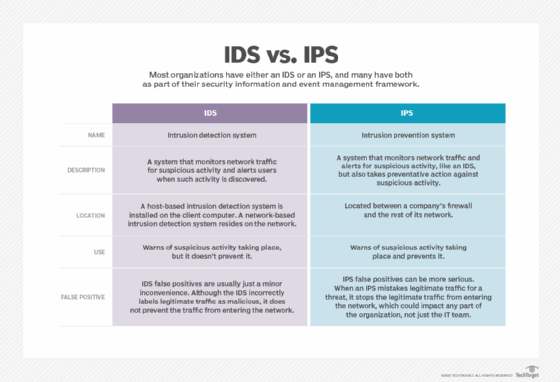
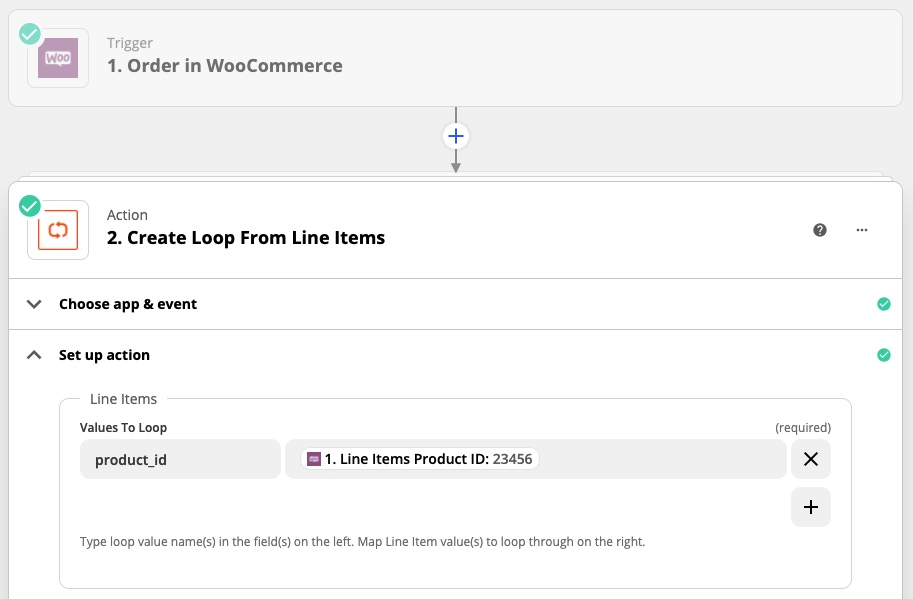


















Post a Comment for "An Active Ids System Often Performs Which Of The Following Actions"